Did you know that nearly 98% of cyberattacks employ social engineering? Cybercriminals use psychological ploys and deceit to sway people or groups. They aim to get them to reveal important data or to do things that could harm them or the company they’re with.
This guide dives into the various social engineering attacks. It equips you with tools to safeguard against these tactics. Be it phishing, pretexting, tailgating, or other deceptive forms, it’s vital to know and defend yourself in the modern digital world.
Key Takeaways:
- Beware of the prevalence of social engineering attacks, which are used in 98% of cyberattacks.
- Understand the various types of social engineering tactics, such as phishing and pretexting.
- Implement best practices to protect yourself from manipulation and deception.
- Educate yourself and others about the risks and indicators of social engineering attacks.
- Stay vigilant and skeptical of unsolicited requests for sensitive information or urgent actions.
What is Social Engineering?
Social engineering is a deceptive tactic used by cybercriminals to manipulate individuals or groups. They aim to make people reveal sensitive information or act in ways that can harm their organization. This tactic is widely used to gain access to login details, financial data, and more. The attackers trick their victims mainly through emails, phone calls, and text messages. Techniques like phishing, pretexting, and tailgating are used to deceive people and use their vulnerability for nefarious ends.
The main goal of social engineering is to get people to share private details like logins or financial info. Attackers take advantage of human nature, using manipulation and deception to build trust. They create convincing messages and scenarios to dupe individuals into disclosing confidential information.
Phishing is a common social engineering attack through fake emails or websites. They are made to look real to gather sensitive details. Pretexting involves creating a false identity to gain the trust of a person. Tailgating is physically following someone into a restricted area. These methods show how cybercriminals exploit human trust and curiosity to get access to valuable data.
To protect against social engineering, it’s crucial to be careful and informed online and offline. Learning about the latest scams and teaching others can help. Use strong security methods, like multi-factor authentication, to protect against attacks. By staying proactive and well-informed, the safety of important data can be ensured against threats.
Key Points:
- Social engineering involves manipulating individuals to reveal sensitive information or perform actions detrimental to their organization.
- Attackers use techniques like phishing, pretexting, and tailgating to deceive victims and gain unauthorized access.
- Vigilance, education, and robust security measures are essential in defending against social engineering attacks.
Types of Social Engineering Attacks
It’s crucial to know the various types of social engineering attacks for self-protection. Understanding the manipulative tactics helps defend and protect our sensitive information effectively.
1. Phishing
Phishing stands as a prevalent form of attack. It uses fake emails or sites to deceive people into sharing sensitive data. Impersonating trusted sources, like banks, these emails lead to identity theft or financial losses. Tackling emails from unknown sources with care is key to avoiding phishing attempts.
2. Pretexting
Pretexting employs a fabricated identity to gain victims’ trust and extract confidential data. It might be a fake colleague or IT specialist. Being mindful of unusual requests for data helps in avoiding pretexting schemes.
3. Tailgating
Tailgating involves entering secure areas without permission, either physically or digitally, through unchecked network access. Cybercriminals use trust or politeness to their advantage. Strong security policies and training are essential for firms to counter tailgating attempts.
4. Baiting
Baiting entices victims with rewards or benefits to disclose information or perform actions. It can be through physical media or online enticements. Avoiding unknown links or suspicious downloads is crucial to thwart baiting schemes.
5. Quid Pro Quo
In quid pro quo attacks, attackers offer something for confidential data or system access. They might do it over the phone or in person, impersonating helpful experts. Staying skeptical and adhering to security procedures helps in steering clear of such attacks.
It’s vital to be well-versed in the types of social engineering attacks for personal and organizational security. Knowledge empowers individuals to stay alert, be cautious in all interactions, and prevent themselves from falling for cybercriminals’ strategies.
Phishing Attacks
Phishing st ands out as a prevalent social engineering method. It leverages deceptive emails and websites to deceive targets. These targets may unknowingly share sensitive data or undertake actions against their interest. Such attacks often rely on urgency or fear to compel victims to act as desired.
ands out as a prevalent social engineering method. It leverages deceptive emails and websites to deceive targets. These targets may unknowingly share sensitive data or undertake actions against their interest. Such attacks often rely on urgency or fear to compel victims to act as desired.
Guarding against phishing requires vigilance towards unsolicited emails seeking personal information or urging link clicks. It’s crucial to confirm the sender’s legitimacy by comparing their details to known contacts. With this, you can avoid falling for false communications or malicious links.
Deploying spam filters contributes significantly to preempting phishing emails. These filters can sift out potential threats before they clutter your inbox. Beyond that, it remains imperative not to disclose sensitive information through email. Genuine entities seldom request such details via this medium.
For fortified defenses, adopting complex, distinct passwords for your various accounts is paramount. This practice strengthens your shield against phishing methods. Regularly updating your software also seals off pathways for attackers to exploit.
Enhanced caution is required for critical tasks like online banking or shopping. This becomes even more critical in the context of public Wi-Fi, which poses a risk for potential interception. Diligence in such scenarios is crucial to prevent data compromise.
- Be cautious of unexpected emails
- Verify the sender’s identity before responding or clicking on links
- Use spam filters
- Avoid sharing personal or financial information via email
- Use strong and unique passwords
- Keep software up to date
- Be cautious when accessing sensitive information on public Wi-Fi networks
Tailgating Attacks
Tailgating, or “piggybacking,” is a deceptive strategy. It involves engaging someone to gain entry into a secure location without proper permission. This may occur physically or by leveraging an unsecured network. The success of tailgating hinges on the victim’s misplaced trust or the false belief that they are accompanying an authorized person into the restricted area.
To ward off these insidious attacks, several countermeasures are vital:
- Deploy physical obstacles to regulate passage through secure entry points.
- Utilize surveillance equipment, such as security cameras, to oversee potential ingress points.
- Educate your staff to recognize and rebuff attempts at unauthorized access through tailgating.
- Enforce a “buddy system,” requiring pairs to jointly access and vacate restricted zones.
- Adopt electronic access systems that validate entrants’ identities before allowing entrance.
By diligently applying these preventive techniques, entities can drastically mitigate the threat of intruders infiltrating their secured premises.
Baiting Attacks
Baiting is a tactic of social engineering, exploiting human vulnerabilities with promises or rewards. It’s used to manipulate us into sharing information or performing risky actions. These attacks exploit our desires, including greed, curiosity, or the search for something better. Infected flash drives may be left out in the open, or we could be tempted by alluring ads or offers.
Defending against baiting attacks requires caution and skepticism. Here are some key tips:
- Always be skeptical of offers that sound too good to be true. Remember, the most exceptional deals are often a trap.
- Never click on unknown links or download files from untrusted sources. Such items might promise rewards but actually hide harmful software.
- It’s essential to educate yourself and others on the perils of baiting tactics. Increasing awareness is critical in fighting off deceitful schemes.
By staying alert and well-informed, you can shield both yourself and your vital information from these cunning attacks.
Pretexting Attacks
Pretexting is a tactic used by cybercriminals to trick people into giving away sensitive info or unauthorized access to systems. They create a false identity or story matched to the victim’s interests. This makes the victim more likely to trust them. The deception can happen face-to-face, over the phone, or through online platforms. Therefore, it’s essential to be alert across all communication methods.
Scammers might pretend to be bank representatives or government officials to get people to share their secrets. They play on our natural willingness to aid and trust others. For instance, they could ask for personal or bank details, passwords, or system access. This targets the victim’s good intentions to help, making them potentially more vulnerable.
To defend against pretexting attacks, be careful with unknown phone calls and emails. Never share personal or financial data with them until you’re sure of the caller or sender’s identity. Make sure you use sturdy, unique passwords and keep all your software up to date. This will help close any security holes that attackers might use.
Here are some tips to avoid falling prey to pretexting attacks:
- Be cautious of unsolicited phone calls or emails.
- Do not disclose personal or financial information in response to unsolicited requests.
- Verify the identity of anyone who requests sensitive information.
- Use strong and unique passwords for all accounts.
- Regularly update your software to ensure security patches are applied.
By adhering to these guidelines, you can lessen the threat of falling for pretexting attempts. This will help keep your personal information safe from malicious actors.
Real-life Example: Pretexting Attack
Kevin Mitnick, a well-known hacker, used pretexting to gain access to confidential data. He was previously on the FBI’s most-wanted list. His strategy involved assuming false identities to exploit people’s trust. Through psychological control, he was able to compromise important systems and extract valuable data.
Scareware Attacks
Scareware, a form of social engineering, plays on our fears and the need to act quickly. It involves fake websites, emails, or pop-ups. They create a false sense of danger, warning us of non-existent malware or threats to our personal data. The intent is to deceive us into buying a fake product or sharing our personal details.
To guard against scareware, vigilance is key. When you spot a suspicious online message, tread carefully. Here are some fundamental tips to protect yourself:
- Avoid clicking on links or downloading attachments from unfamiliar or unreliable sources. Scareware attackers use these avenues to spread their harmful content.
- Keep your software up to date by promptly updating. These updates often contain security features that keep you safe from the latest scareware.
- Be wary of pop-up windows or messages that warn about security threats on your device. Always double check the legitimacy of these claims with trusted sources before proceeding.
By heeding these protection tips, you can greatly reduce the risk of scareware threats and safeguard your personal data.
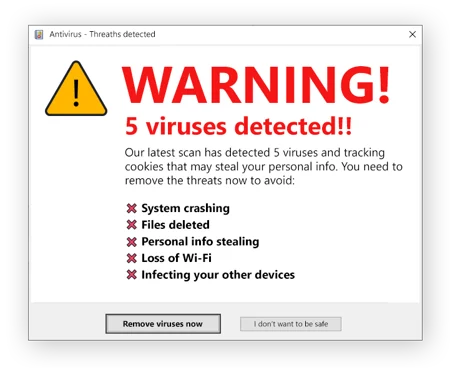
Example Scenario: False Alarms and Fictitious Threats
Scareware typically uses false threats and alarms to pressure individuals into immediate action. A classic example is a pop-up announcing that your computer is virus-ridden. It then prompts you to buy a sham antivirus program. The aim is straightforward: exploit your fears and coax you into interacting with the attacker.
Another method includes misleading emails or fake ads warning of huge financial losses or identity theft. These scare tactics push individuals to either disclose personal data or make rash buy decisions.
Remember, legitimate security warnings never solicit personal info or immediate payments. Stay sharp and skeptical. By doing so, you can fend off scareware ploys and sidestep their manipulative advances.
Quid Pro Quo Attacks
Quid pro quo attacks fall under the umbrella of social engineering, a method used by cybercriminals. In this tactic, they offer something valuable to trick people into sharing sensitive information or system access. These exchanges happen over the phone or in person, often seeming like a normal request or favor. The success of such attacks comes from the victim’s trust in the apparent benefit offered.
For individuals and organizations, vigilance is key in warding off quid pro quo attacks. Following some crucial preventative measures can significantly reduce the risk:
- Be wary of deals that sound too good to be true. Anything that seems overly convenient or beneficial may actually be a warning sign.
- Avoid giving out personal or financial data in response to unsolicited demands. Legitimate entities won’t press for confidential details without a clear, valid necessity.
- Create and use robust, unique passwords. Never reuse these across your various accounts to keep your systems safe from unauthorized entry.
- Keep your software up to date to enjoy the latest security defenses against recognized loopholes and threats.
By strictly adhering to these pointers, you can fortify your defenses against quid pro quo attacks. This approach helps safeguard your personal and organizational sensitive information more effectively.
Quid Pro Quo vs. Phishing Attacks
Quid pro quo and phishing attacks both lie within the realm of social engineering but employ different strategies. The former offers a benefit in return for access or information, while the latter uses deceptive emails or websites to deceive individuals. Recognizing these differences can enhance your capability to distinguish between and combat various social engineering threats effectively.
A Comparison of Quid Pro Quo and Phishing Attacks
| Aspect | Quid Pro Quo Attacks | Phishing Attacks |
|---|---|---|
| Method | Offers something in exchange for sensitive information or access | Uses deceptive emails or websites to trick victims |
| Medium | May occur over the phone or in person | Typically initiated through email communications |
| Deception | Disguises the offer as a legitimate request or favor | Creates fake emails or websites impersonating trusted entities |
| Aim | Obtains sensitive information or unauthorized access | Tricks victims into divulging their information |
| Response | Relies on the victim’s willingness to provide information | Relies on the victim’s action (clicking on a link, downloading an attachment) |
Creating a Human Firewall
Establishing a human firewall is vital to fend off social engineering attacks. Organizations empower their staff through education. They learn to recognize and combat tactics like phishing and pretexting.
Educational Initiatives
Education stands at the forefront against social engineering. Employees benefit from regular sessions and awareness activities. This equips them to spot threats, grasp attacker methods, and reduce risks efficiently.
Training involves sharing real cases and fostering understanding through interactive tasks. This method strengthens the human firewall. It reduces the threat of successful social engineering attacks.
Recognizing Social Engineering Tactics
Awareness is crucial in identifying and responding to these tactics. Staff learns about the common signs of phishing and pretexting. This includes:
- Requests for sensitive information via emails or messages.
- Clickable links or downloads from unfamiliar sources.
- Demands for personal login credentials, financial details, or confidential data.
- Messages that instill a sense of urgency or fear, appearing out of context.
Encouraging vigilance and critical thinking makes employees an integral part of the organization’s defense. They are urged to think before acting in questionable situations.
Reporting and Response Procedures
Clear procedures for reporting and responding are the backbone of a human firewall. Staff must know how to report suspicious activities. They should be familiar with designated contacts, which may include IT security teams or response hotlines.
Incident response plans are also key. Organizations need defined steps for handling and recovering from social engineering strikes. This includes isolating affected devices, informing stakeholders, researching the incident, and applying safeguards for the future.
Continuous Improvement
A dynamic human firewall keeps up with new social engineering tactics. Organizations promote continual learning among employees. This involves staying informed on attack variants, adopting best practices, and practicing with simulations.
| Benefits of a Human Firewall | Actions to Strengthen the Human Firewall |
|---|---|
| Enhanced protection against social engineering attacks | Regular training and awareness programs |
| Increased employee confidence in identifying and reporting potential threats | Establishing clear reporting and response procedures |
| Institutionalizing a culture of security consciousness | Continuous improvement through ongoing training and resources |
| Minimizing the risk of data breaches and unauthorized access | Fostering a collaborative and vigilant workforce |
Building a robust human firewall involves various efforts. From education to continuous enhancement, it’s multi-faceted. A strong human firewall is pivotal for a top-tier defense strategy.
Slowing Down and Asking Questions
When protecting oneself from social engineering attacks, slowing down and asking critical questions are vital. Assessing digital messages carefully can unveil inconsistencies or flags of potential deception. It is essential to be skeptical, which aids in staying alert and cautious.
Questioning the authenticity of requests for sensitive details or immediate action is a strong defense. Trust your gut when something appears dubious. Confirm the sender’s identity using recognized communication methods or by verifying with company guidelines. This ensures you engage safely.
Social engineering capitalizes on trust to deceive and coerce individuals into actions against their interest. A skeptical, questioning stance is a powerful defense against such manipulations.
In conclusion, adopting a critical, questioning approach is key to thwarting social engineering. By scrutinizing digital interactions, embracing skepticism, and validating requests, you protect yourself from potential harm.
Conclusion
Defending against social engineering demands awareness, skepticism, and technology. It’s crucial to comprehend the psychology behind these attacks. With this knowledge, people and groups can deploy defenses that significantly reduce the threat.
Training is key in readying employees to spot and counter social engineering. This involves tactics like phishing and pretexting. Embedding strong security practices across all aspects, whether physical or digital, further fortifies against breach.
Bearing caution on social media is a must, given it’s a hub for intel gathering by attackers. Being cautious in sharing personal data and reviewing connection requests is a powerful preventive step against social engineering.
Although individual awareness is critical, technological tools also bolster defense. Features like email filters, multi-factor authentication, and dedicated security training are invaluable. They add layers of protection against manipulation.
In sum, defense against social engineering requires a multi-faceted strategy blending human awareness with advanced defenses. By continuously educating and staying alert, individuals and groups can establish solid barriers against social engineering exploits.



